VeriCapture
Evidence Generation Tool
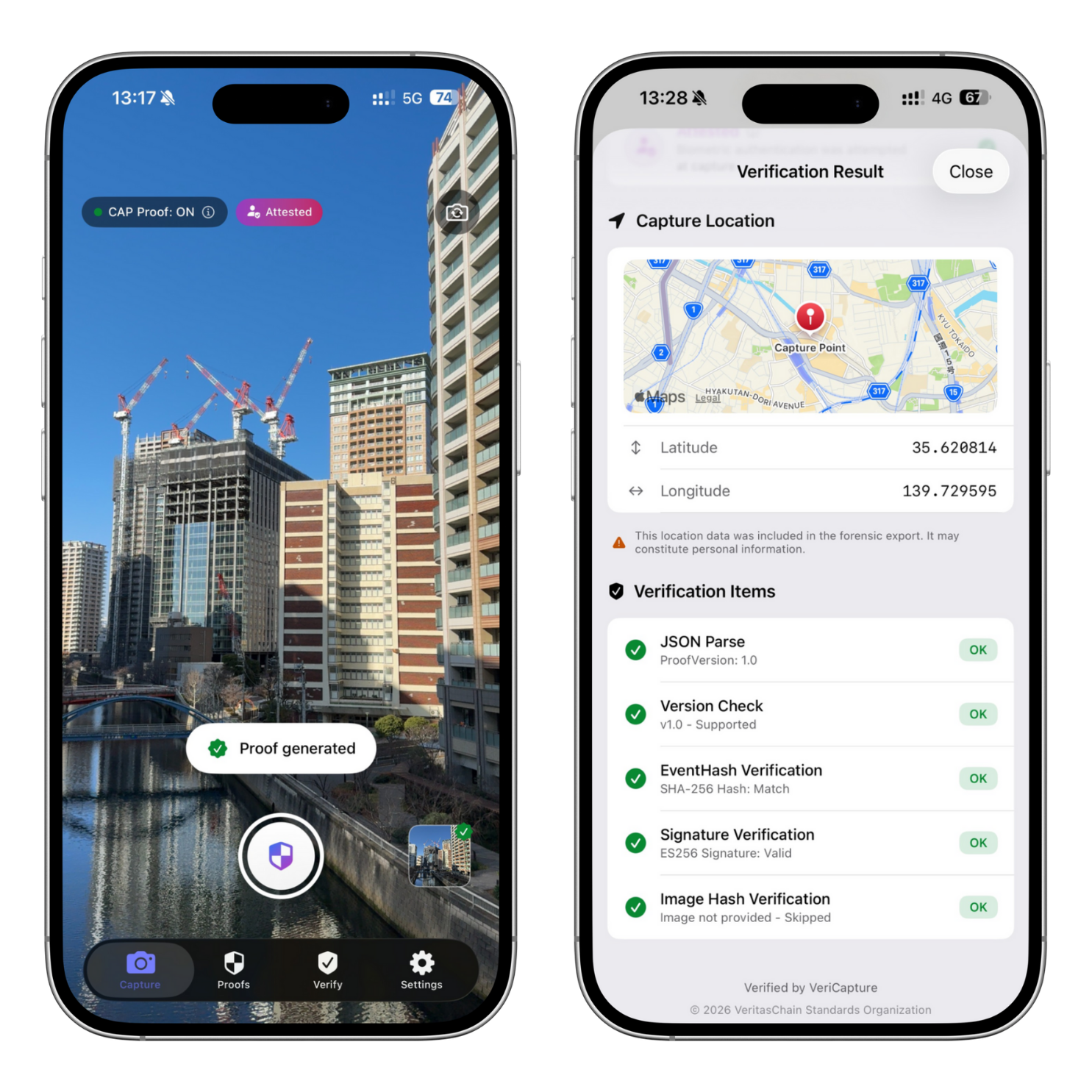
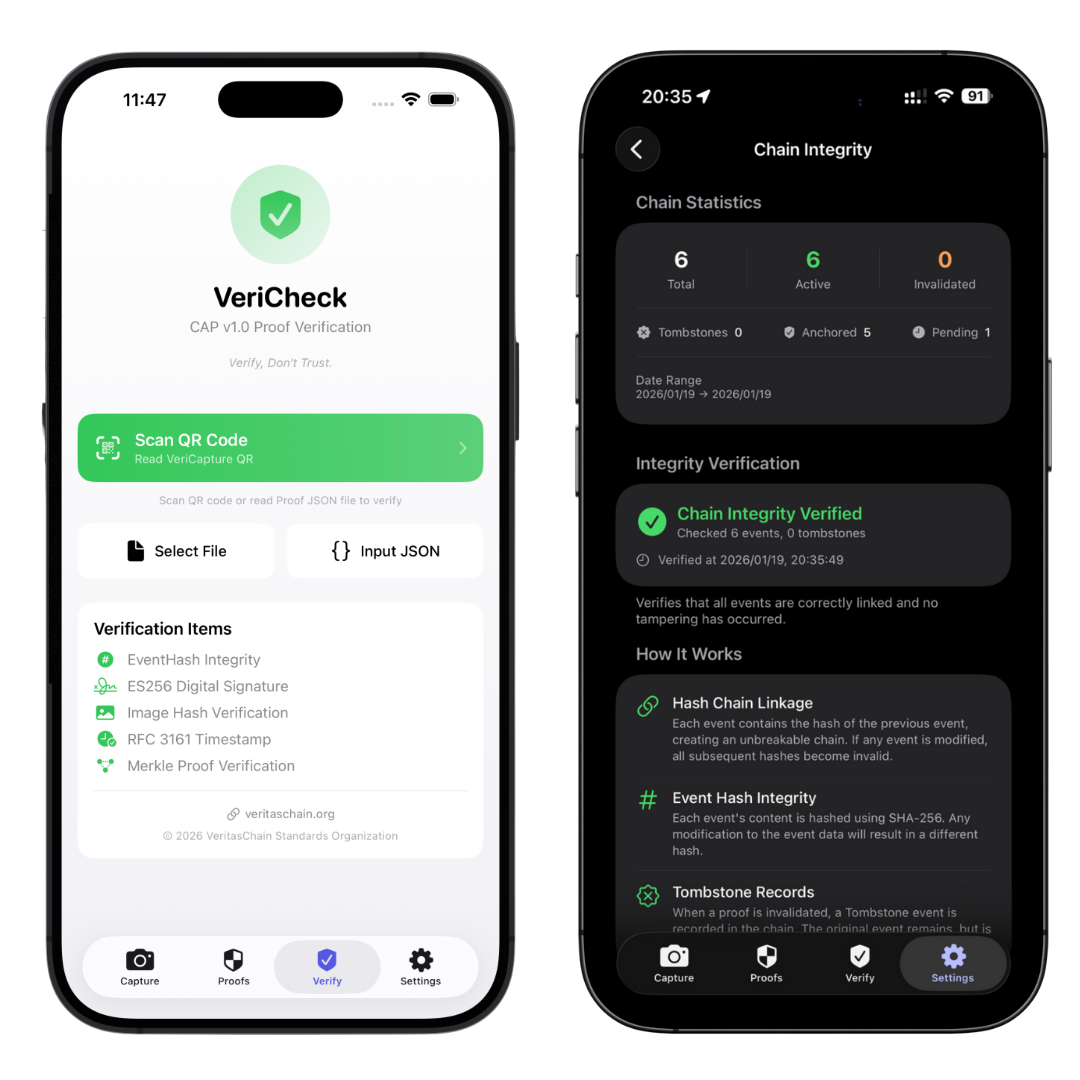
"Record capture events and data provenance in a cryptographically verifiable manner."
What VeriCapture Records
- The fact that a capture operation occurred
- Provenance data (hash, timestamp, signature)
- Tamper detection capability
- Third-party independent verification
What VeriCapture Does NOT Provide
- Truth verification of content
- Legitimacy guarantee of subjects
- Identity verification / personal authentication
- Fake detection / anti-fake capability
Verify, Don't Trust.
— Mathematical verification, not trust-based assumptions
Utilities / Business — NOT in Photo & Video category. VeriCapture is a specialized professional tool, not a general consumer camera app.