VeraSnap
Evidence Generation Tool — CPP v1.4 Compliant iOS Application
VeraSnap
Evidence Generation Tool
VeraSnap is NOT a camera app. It's a professional evidence generation tool that cryptographically records capture events and data provenance in a tamper-evident manner.
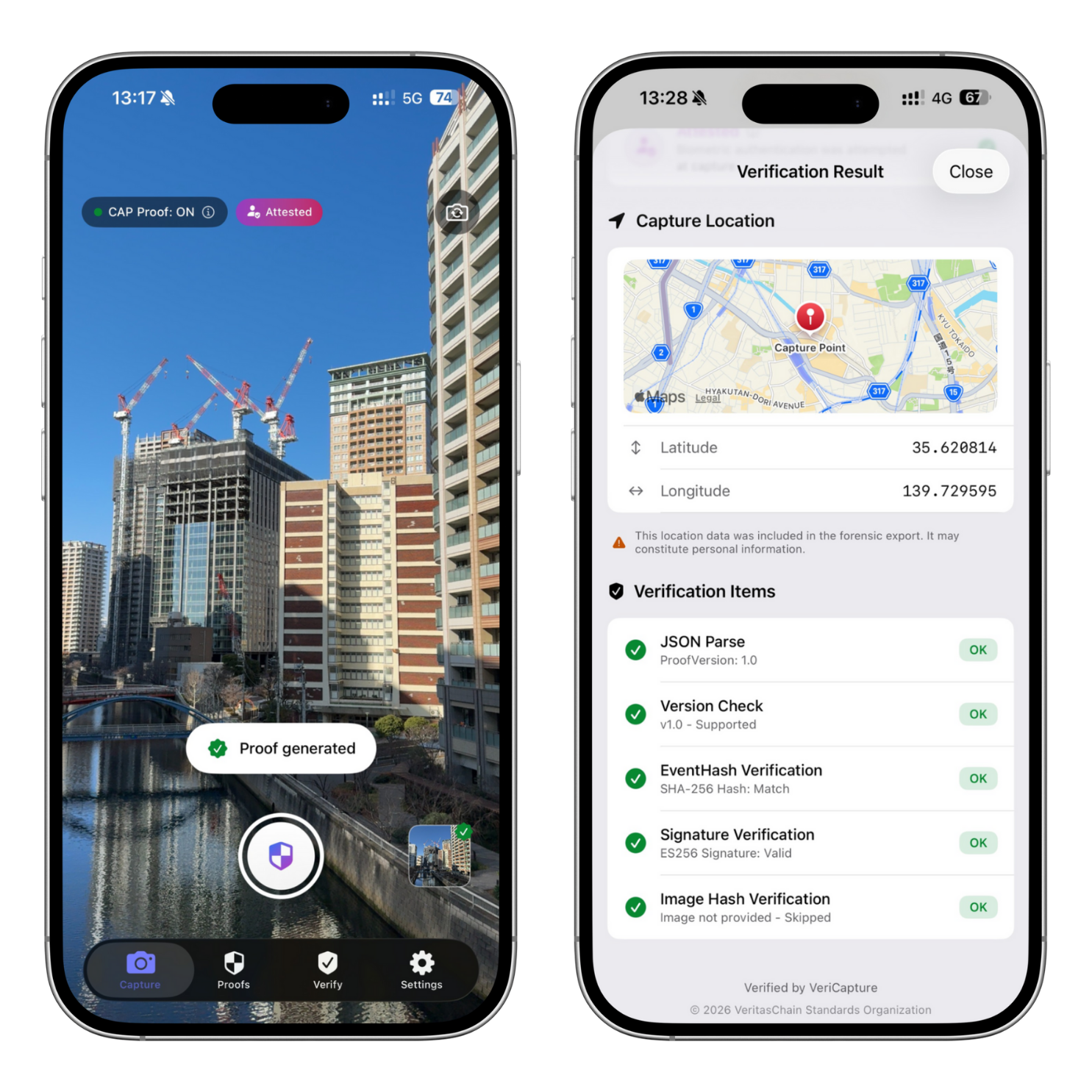
"Verify, Don't Trust."
Important: VeraSnap records capture events — it does NOT verify content truth or legitimacy.